Foxx
The Living Force
chaps23 said:_https://www.torproject.org/projects/torbrowser.html.en
This program for anon browsing. No one will no what your up to, and if there are certain sites you cant access due to your country of origin you can bounce a relay off that country to gain access to the site, this software is excellent and all of us should be using it.
TOR happens to be one of my pet peeves as it's yet another thing that's marketed to people as being on the side of the "good guys", but people don't know anything about how it works, how and why it's vulnerable to attacks, and basically just suspend their brains while believing that they can avoid being monitored (which isn't possible at all since there are probably backdoors in every operating system--including open source operating systems--and the hardware of every computer ever produced).
_http://sheddingbikes.com/posts/1293530004.html
The Sordid Past And Present Of Tor
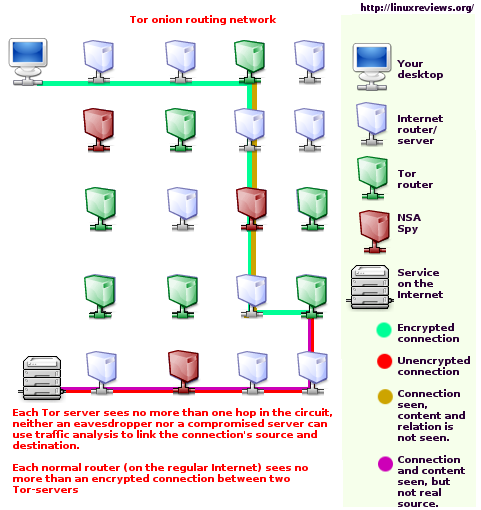
Tor by itself, without knowing its history, seems like a great idea. You point your browser at it and suddenly you can view web pages without people knowing that it's actually you. Great right?
The problem is that Tor's pedigree is less than stellar. First, it was originally a US Navy project then released to various "hackers" (a word which in a lot of ways is just synonymous with "NSA collaborator" or at least a wannabe). Whether the source code started there or just the idea, you have to ask why the hell the Navy would work on this and then release it.
The Navy of course gave some hand-wavy answer of wanting to use it, but the Navy just doesn't do something like this without another reason. Who knows what it is, but I this makes my spidey sense go off.
That's the first strike against Tor, but let's look at more reasons to not use Tor. How about the research that showed how easy it is to break in various ways. Those might be fixable, so how about that there can be super nodes that with just a small sample of traffic can figure out a lot of content?
Alright, maybe that can be fixed, but then you read about a semi-secret volunteer group collecting data from 12 ISPs and handing it to the government. This Project Vigilant apparently has 600-1500 volunteers who are all hackers collecting and analyzing data and handing it straight to the government without user consent. Project Vigilant also claims it:
tracks more than 250 million IP addresses a day and can "develop portfolios on any name, screen name or IP address."
Holy crap, that's a lot of traffic analysis. Given how small the "hacker" community is, that's also a gigantic percentage of hackers and security experts on the volunteer payroll of a group who's job is to illegally wiretap people and circumvent the law on behalf of the government.
(there are embedded links on the page not included in the quote)
There are also actual documented examples of nodes performing "man in the middle" attacks (inserting themselves in between you and your encrypted destination and capturing all the data that you believe is being securely transmitted between you and the end point):
_http://www.teamfurry.com/wordpress/2007/11/20/tor-exit-node-doing-mitm-attacks
I decided to do some more digging on the TOR network to see whether there really are exit-nodes doing MITM attacks. As a target site, I picked up my home computer that had an SSL enabled server.
...
I ran through all the exit-nodes in my current directory cache, connecting to my website and saving the certificate. After that I compared the certificates to see whether I picked up any that were different from the real SSL cert on my site. One certificate differed from the original:
...
So, what we have here is an TOR exit-node that is doing Man-In-The-Middle attacks on HTTPS connections.
Commentary on that:
_http://www.schneier.com/blog/archives/2007/12/maninthemiddle.html
EDITED TO ADD (12/6): The guy claims that he just misconfigured his Tor node. I don't know enough about Tor to have any comment about this.
...
jeremiah • December 6, 2007 2:35 PM
I love how programs that people believe will increase security, actually decrease it. Wait, no, that's hate. I hate those programs.
@Andy: he didn't just self-sign his certificate, he's using it to impersonate folks whose WWW connections are coming from his exit node. He impersonates the client for the server, and impersonates the server for the client, and he holds all the SSL keys that are used in the encryption. He is then able to see all the https traffic coming in and out of his exit node in clear text. Man in the middle.
He has everything he needs to fetch out all kinds of personal information, and using that information fraudulently is a breeze.
It's not possible to "misconfigure" a node in such a way--it's intentional and the issue is that TOR doesn't prevent it from happening.
And this is really the key that TOR isn't secure:
_http://www.i2p2.de/how_networkcomparisons.html
Benefits of I2P over Tor
Peers are selected by continuously profiling and ranking performance, rather than trusting claimed capacity
If one wants power in TOR, one sets up a node, claims that they have tons of capacity, and then get tons of traffic routing through it just because they said that they have lots of capacity and TOR and its users blindly believe it. Obviously this is one of the worst places to place trust and any alphabet soup agency can, and most assuredly does, setup such a node and then monitor all the people who think they're outsmarting those agencies (along with monitoring them in a million other ways).
So essentially, TOR doesn't offer any additional security, has known exploits and fundamental flaws, is known to be being exploited currently, and has government ties--its entire story is false, so I think the real reason that it's around is some nefarious thing.
The simple reality of computer security against TPTB is that there is none. For actual computer security, you'd have to build the hardware yourself from the ground up (and I don't mean assemble, I mean design and manufacture each individual part yourself), do the same with the software, AND never let it out of your sight so someone doesn't install something malicious while you're away for 5 minutes. Even then there are still plenty of ways for your data to be compromised--the problem is, there's always a weak link. It is possible to have security against some average joe hacker or identity thief or whoever, so some security steps are valuable for that reason, but there's no defense against the control system in terms of computer security and they already know everything you're doing.
As an addendum, to point out that probably every operating system has a backdoor in it:
_http://sheddingbikes.com/posts/1293530004.html
P.S. I have a long bet that SELinux is an NSA backdoor. Any takers?
I'm definitely one.
_http://en.wikipedia.org/wiki/Security-Enhanced_Linux
The key concepts underlying SELinux can be traced to several earlier projects by the United States National Security Agency.
It has been integrated into the mainline Linux kernel since version 2.6, on 8 August 2003.
...
NSA Security-enhanced Linux is a set of patches to the Linux kernel and some utilities
Windows and Mac OS X are closed source operating systems, so putting a back door in them is trivial (I'd say there's basically a 0% chance that they don't have at least one). Linux is open source, but even it has had code written specifically by the NSA for almost a decade and this code is distributed with basically every version of linux out there.
It doesn't matter what lock you put on, they have a skeleton key (though again, context matters--a lock can potentially stop the average criminal).
And this is all just from what we know--it's essentially a given that they have technology dramatically past what we're aware of, which may render all of this even more moot.
chaps23 said:No one will no what your up to
If they want to know, they'll always be able to know.