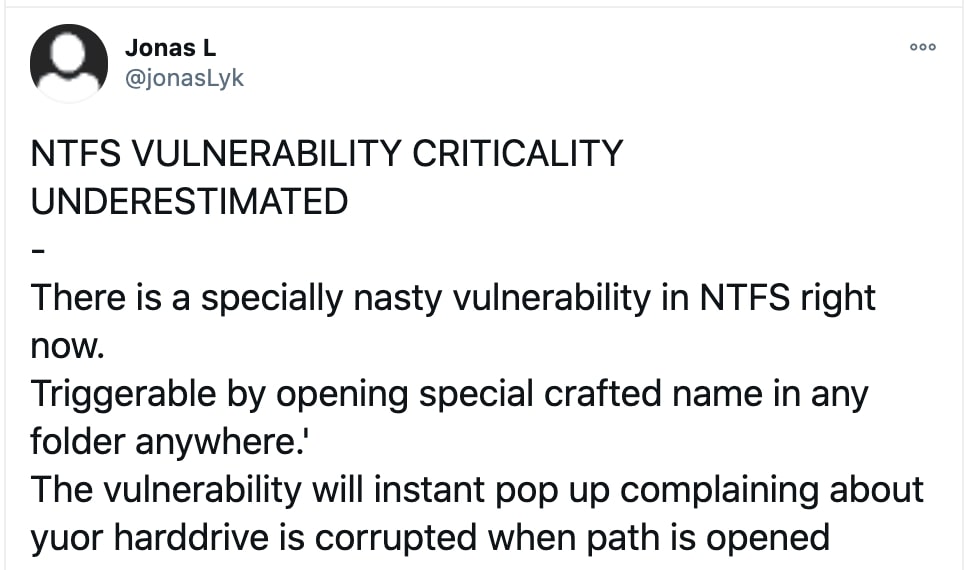
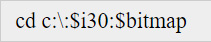
Thought it might be worth getting ahead of this one. Given the 'covid pandemic' followed the World Economic Forums simulated "Event 201" The Event 201 scenario | A pandemic tabletop exercise - we have other table top simulations to look forward too.
The Cyber Polygon was first held in 2020, and the next event will be July 9th 2021.

 www.weforum.org
www.weforum.org
So what we can probably glean from this is:
1) A whole bunch of scary cyber attacks. Supply chain disruptions (great for covering the actual supply chain disruptions caused by lockdowns). Probably a whole bunch of power/water/monetary (can't buy food or fuel) outages. A good chance that lots of smaller businesses get 'picked off' and taken out - as well as 'problematic websites'.
2) More jobs will be offered in IT/security, as this was mentioned as part of the Great Reset plan.
3) Digital ID's/passports will likely be proposed as 'the solution'.
4) Given the food shortages and lack of jobs/money - this ID will probably grant you food (vegan, with a calorie limit) and 'universal basic income'. Assuming you are a 'good vaccinated citizen who doesn't make trouble'.
5) As always it'll be linked to getting rid of meat production and 'being green'.
I've seen a lot of articles over the last few years that line up with preparing the population to accept these narratives (might be worth collecting some here?). Here's just one of the latest:

 www.news.com.au
www.news.com.au
The Cyber Polygon was first held in 2020, and the next event will be July 9th 2021.

Cyber Polygon
These days, as the digitalisation is gathering pace, ecosystems are more widespread than ever. The interconnectedness between industries and countries is growing, while companies are taking the expansion of their supply chains to a global scale. In this context, the vulnerability of one...
Digitalisation is accelerating everywhere. New digital ecosystems are forming all around us, creating unnoticed linkages across services and supply chains.
As the world grows more interconnected, the speed of development makes it difficult to assess the impact of change.
A secure approach to digital development today will determine the shape of our future for decades to come. Having the right skills in place is key to protecting organisations from attack now.
What is Cyber Polygon?
Cyber Polygon is a unique cybersecurity event that combines the world's largest technical training exercise for corporate teams and an online conference featuring senior officials from international organisations and leading corporations.
The 2021 conference discusses the key risks of digitalisation and best practice for the secure development of digital ecosystems.
The 2021 technical exercise builds and tests the skills needed to protect our industries, centring on a targeted supply-chain attack.
Every year, the training brings together a global businesses and government agencies to collaborate on technical exercises. The live stream draws in millions of spectators from across the world.
2020 results
120 teams from 29 countries took part in the technical cybersecurity training in 2020. The live stream viewership reached 5 million from 57 nations.
A comprehensive report with detailed results of Cyber Polygon 2020 is available here.
Cyber Polygon in 2021
This year discussions during the live-streamed conference will centre on secure development of ecosystems. With global digitalisation further accelerating and people, companies, and countries becoming ever more interconnected, security of every single element of a supply-chain is key to ensuring the sustainability of the whole system.
During the technical exercise, participants will hone their practical skills in mitigating a targeted supply chain attack on a corporate ecosystem in real time.
The event will be held online on July 9th. Applications from organisations wishing to join the training are open. See further details on the official website.
Averting a cyber pandemic: how businesses are building a global response to cybersecurity risks
Published
28 Jan 2021
The impact.
The World Economic Forum’s Centre for Cybersecurity has created a community of security and technology leaders to identify future global risks from next-generation technology in order to avert a cyber pandemic.
What policies, practices and partnerships are needed to prevent such a cyber pandemic? This question was raised in sessions on Thursday 28 and Friday 29 January at the Davos Agenda 2021, featuring commentary from Check Point Software Technologies, Cloudflare, Fortinet, INTERPOL, Cyber Security Agency of Singapore and AustCyber.
The Forum has created Future Series: Cybercrime 2025, a joint program of work with the University of Oxford - Oxford Martin School, enabling organizations to share and develop research, insights and responses to future risks as a community.
The initiative convenes over 150 global experts from the world’s leading companies, research institutions and public-policy departments. Major collaborators include Palo Alto Networks, Mastercard and KPMG, and support from such institutions as Europol, ENISA and NIST.
The first findings and recommendations of the community’s work were recently published in the Cybersecurity emerging technology and systemic risk report.
"There must now be a different approach to cybersecurity. Our current approach is unsustainable."
Ken Xie, Founder, Chairman of the Board and Chief Executive Officer, Fortinet
What's the challenge?
The critical technology transformations on which future prosperity relies – ubiquitous connectivity, artificial intelligence, quantum computing and next-generation approaches to identity and access management – will not just be incremental challenges for the security community.
Unless action is taken now, by 2025 next-generation technology, on which the world will increasingly rely, has the potential to overwhelm the defences of the global security community.
Next-generation technologies have the potential to generate new risks for the world, and at this stage, their full impact is not well understood. There is an urgent need for collective action, policy intervention and improved accountability for government and business.
Without these interventions, it will be difficult to maintain integrity and trust in the emerging technology on which future global growth depends.
What would be the global impact of a digital virus compared to a biological one?
Our approach.
The Future Series: Cybercrime 2025 initiative was launched by the World Economic Forum to identify what approaches are required to manage cyber risks in the face of the major technology trends taking place in the near future:
Skills gap.
There is already a global capacity shortage in cybersecurity (specialists and throughout the wider workforce) and as new technologies emerge, the skills gap in delivering cybersecurity will widen. [*note - The Great Reset mentions most people will need to retrain for IT jobs *]
Fragmented approaches.
Emerging technologies are driving an increasing interdependence and entanglement between policy and technology at a time when the global governance of cyberspace is weak.
New approaches.
Existing operational-security capabilities and technologies will not be fit for purpose, so mitigating threats and responding to incidents individually and collaboratively will require new approaches.
Underinvestment.
Security is not being considered as an integral component of technology innovations and as such, proper investment is not being made into support (knowledge, guidance, research investment) and incentives (market forces, regulation) for developing emerging technologies securely.
Ambiguous accountability.
Shared dependence widens the pool of actors affected by the resilience of a part of the ecosystem, built can also create ambiguity in the accountability for ensuring this resilience.
The World Economic Forum’s Centre for Cybersecurity is calling on the global community to implement the recommendations made in its Future Series report.
“Security must be more proactive and future-proof if we are to out-innovate the attackers.”
Nikesh Arora, Chief Executive Officer and Chairman, Palo Alto Networks, USA
How can you get involved?
A new approach to cybersecurity is needed. The security and technology community, industry and government leadership and the international community must intervene to ensure that security issues are addressed in such a way that the benefits of emerging technology are inclusive.
Companies can join the Forum's efforts to tackle the range of complex industry-wide challenges. Find out more via the links below.
So what we can probably glean from this is:
1) A whole bunch of scary cyber attacks. Supply chain disruptions (great for covering the actual supply chain disruptions caused by lockdowns). Probably a whole bunch of power/water/monetary (can't buy food or fuel) outages. A good chance that lots of smaller businesses get 'picked off' and taken out - as well as 'problematic websites'.
2) More jobs will be offered in IT/security, as this was mentioned as part of the Great Reset plan.
3) Digital ID's/passports will likely be proposed as 'the solution'.
4) Given the food shortages and lack of jobs/money - this ID will probably grant you food (vegan, with a calorie limit) and 'universal basic income'. Assuming you are a 'good vaccinated citizen who doesn't make trouble'.
5) As always it'll be linked to getting rid of meat production and 'being green'.
I've seen a lot of articles over the last few years that line up with preparing the population to accept these narratives (might be worth collecting some here?). Here's just one of the latest:
JBS meatworks cyber attack shuts down Australia, US and Canada facilities
Major cyber attacks have led to Australia’s largest meatworks company JBS Foods shutting down, as well as their facilities in the United States and Canada, the Queensland meat industry union confirmed.
JBS meatworks cyber attack shuts down Australia, US and Canada facilities
Australia’s biggest meatworks company has been hit by a shock attack – and insiders say it could end up driving up prices for shoppers.
May 31, 20215:31pm
Major cyber attacks have led to Australia’s largest meatworks company JBS Foods shutting down, as well as their facilities in the United States and Canada, the Queensland meat industry union confirmed.
Their information systems were targeted, with the company’s chief executive Brent Eastwood confirming the news to Beef Central.

JBS meat packing has been shut down over cyber attacks. Picture: Getty ImagesSource:Getty Images
The cyber attack means that thousands of people would go without pay, the Australian Meat Industry Employees’ Union Queensland Secretary Matt Journeaux said.
“The meat in the sandwich is that this is a concerted effort against Australian business and the workers will suffer as a result of that,” Mr Journeaux told ABC Radio Brisbane.
“There’s six sites in Queensland that will be affected … and around the nation there would be significantly more.
“In most processing facilities the workers are on daily hire arrangements and unfortunately if they don’t work, they don’t get paid.”
Across Australia the company has 47 sites, operating the largest network of production facilities and feedlots in the country.

The attack may lead to meat shortages. Picture: Getty ImagesSource:Getty Images
The government has since been made aware of the attack, says Federal Agriculture Minister David Littleproud. He confirmed they were working to get JBS meatworks back online nationally.
However, Mr Journeaux explained of a dire possible ramification which could come from this attack if it isn’t resolved soon.
“If this situation isn’t rectified within weeks it would definitely have flow on effects,” he said.
“There could be a protein deficiency globally because of this.”
He went on to explain that every step of processing was down.
“Cattle get entered into systems to be processed,” he said.
“When those cuts are in a box computers print tickets with barcodes for those cuts, and I think all of those systems have been affected by this.”