16.05.2018 - Ecuador Spends some $5 Min to Protect WikiLeaks' Assange - Reports
Ecuador Spends Some $5Mln to Protect WikiLeaks' Assange - Reports
Ecuador spent at least $5 million on a spy operation to support and protect WikiLeaks founder Julian Assange in its embassy in London, media reported.
Documents seen by The Guardian newspaper revealed that millions were put into a secret intelligence operation, dubbed "Operation Guest," and employing undercover agents to monitor Assange's visitors, embassy employees and the UK police.
Moreover, a joint investigation by The Guardian and the Focus Ecuador media outlet showed citing sources that the operation had been approved by former Ecuadorian President Rafael Correa and former Foreign Minister Ricardo Patino.
According to the newspaper,
the security team also recorded the WikiLeaks founder's daily activities in minute detail, as well as his interactions with Ecuador's embassy staff and other visitors.
16.05.2018 - US Officials Name Vault 7 Suspect, Still Lack Sufficient Evidence to Charge Him
US Officials Name Vault 7 Suspect, Still Lack Sufficient Evidence to Charge Him
The identity of the suspected Vault 7 leaker, which detailed the capabilities of US intelligence agencies to manipulate everyday technologies, was revealed to be 29-year-old Joshua Schulte, a former CIA software engineer who designed malware that could break into the computers of suspected terrorists, the Washington Post reported on Tuesday.
There's one problem, though: investigators haven't been able to collect enough evidence to file charges against Schulte despite having searched his apartment and confiscated his personal computer and notes.
According to the New York Times, FBI agents obtained a warrant to search Schulte's apartment in March 2017, a week after WikiLeaks released the first batch of
Vault 7 documents, which highlighted how the CIA tapped into iPhones and smart TVs and turned them into surveillance devices.
Instead of charging Schulte for the leak, prosecutors ended up charging him in August 2017 with possessing, receiving and transporting child pornography after investigators stated they'd found porn content on a server he'd created in 2009. Though he was released a month later in September, Schulte wound up back behind bars by December after violating the rules of his release.
"Those search warrants haven't yielded anything that is consistent with [Schulte's] involvement in that disclosure," Matthew Laroche, an assistant US attorney in the Southern District of New York, said in a January hearing regarding the Vault 7 case.
The Post reported Laroche saying at the time that the investigation was still "ongoing" and that the CIA employee was still a "target."
Schulte has pleaded not guilty to the child porn charges and stated that anywhere from 50 to 100 people had access to the server he'd created in 2009 as a way to share movies and other digital files, according to the publication.
The imprisoned software engineer told the outlet in a statement that he'd been blamed for the leaks because he'd reported "incompetent management and bureaucracy" at the CIA to the inspector general. This, he alleges, made him appear as a disgruntled employee when he left the spy agency in 2016.
"Due to these unfortunate coincidences the FBI ultimately made the snap judgement that I was guilty of the leaks and targeted me," Schulte told the Post for the story published Tuesday.
With Schulte's lawyers demanding prosecutors come to a decision on Vault 7 charges, officials indicated last week that they'd be filing a new indictment in the next 45 days, the Times stated.
"This case has been dragging since August 2017," Sabrina Shroff, Schulte's lawyer, told the outlet. "The government should be required to indict so Mr. Schulte has the opportunity to defend himself. Otherwise he is just languishing."
Schulte is currently being held at the Metropolitan Correctional Center in Manhattan.
May 16, 2018 - Vault 7 Why the CIA sought to get IP-addresses of Russia's Interior Ministry
'Vault 7': Why the CIA Sought to Get IP-Addresses of Russia's Interior Ministry
ikiLeaks, a whistleblowing website,
recently published a massive trove of documents from the CIA, code-named Vault 7. The leaks contain an archive of hacking tools used by the US intelligence agency.
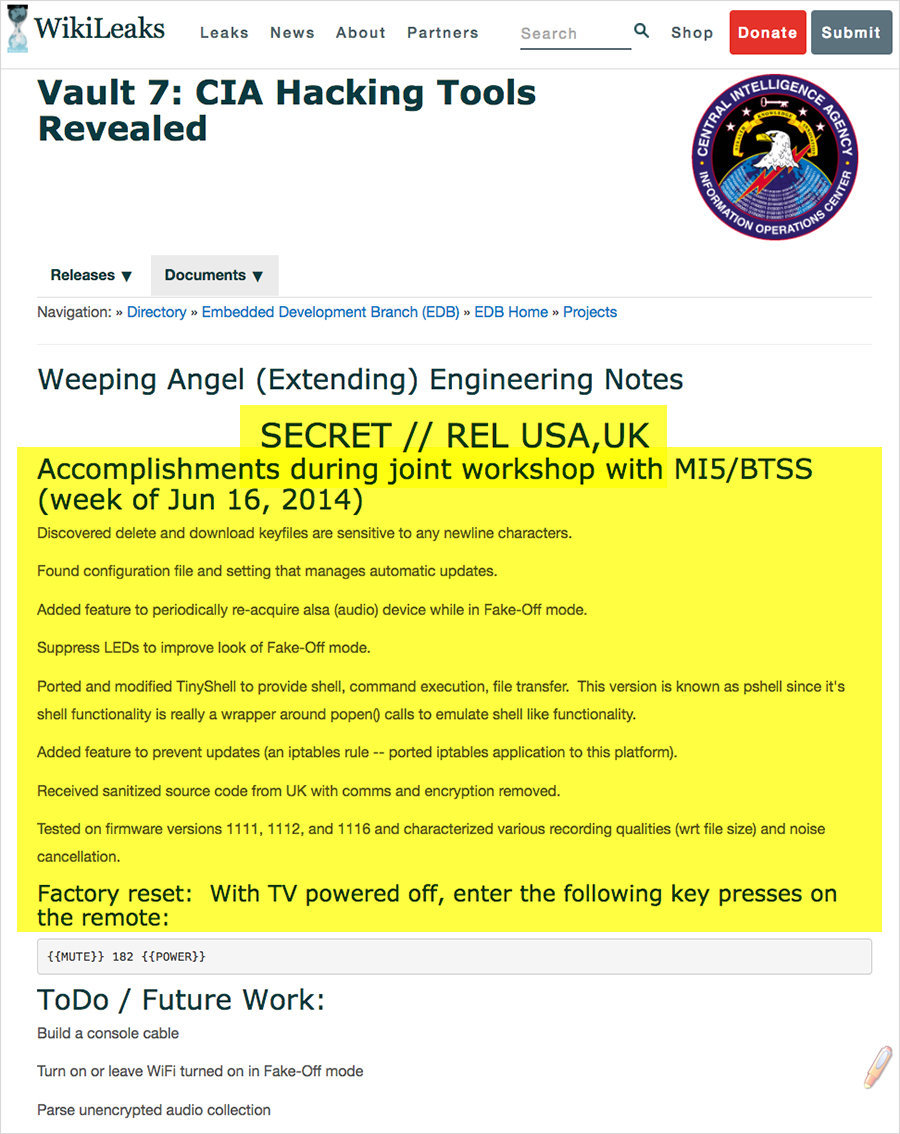
A program created by the CIA, called "Weeping Angel", can wiretap private homes by gaining access to smart TVs
Walls Have Ears
The diversity of hacking instruments at the CIA's disposal is outstanding. Among them are malware and remote control over
Microsoft Windows-powered computers. Devices
powered by iOS are also vulnerable, including the iPhone and the iPad. Calls, messages, emails and photographs on
Android devices are also exposed to tracing and control.
Moreover, the CIA's Embedded Devices Branch (EDB) and the British MI5/BTSS agencies have developed a program called
"Weeping Angel" which can penetrate smart TVs and turn them into covert microphones that listen in on conversations held at home.
In October 2014, the CIA studied
embedding viruses into vehicle control systems. The document does not give a clear answer on the purpose of such procedures, but there is two assumptions that can hardly be ignored – turning a vehicle into a spying device or causing a crash.
Apple was quick to react to the leak, assuring that the majority of the vulnerabilities were outdated, or have already been fixed.
Similar statements were later made by Samsung and Microsoft. Even if some of the vulnerabilities were not fixed before the leak, they will be patched soon.
Thus, the new dump by WikiLeaks has partially disarmed the CIA's cyber-intelligence branch.
Weird Consulate
The documents also reveal that the US consulate in the German city of Frankfurt is used as a
"covert CIA hacker base," with intelligence operatives receiving diplomatic passports and cover from the government. The majority of the CIA hacking tools were developed there.
The consulate itself looks strange. Only a few US embassies are larger than the building in Frankfurt. According to the German newspaper Frankfurter Allgemeine Zeitung, there are some 1,000 personnel in the consulate. It occupies an area of nine hectares and enclosed with a four-meter high barbwire fence.
According to Süddeutsche Zeitung, another German newspaper, in Frankfurt and its surroundings, the US runs a network of front companies as a disguise for intelligence activities.
A special legal status places no limits on US hacking activities at the site. Unlike an embassy, the consulate is not American territory, and thus it does not fall under US jurisdiction, including in terms of protecting privacy.
On the other hand, diplomatic immunity means that activities inside the consulate cannot be checked for compliance with German law.
(A page from the 'Vault 7' archive published by WikiLeaks)
Not Leaving a Trace
The archive of
project UMBRAGE has a special place among the leaked documents. Within this project, the CIA collected information about hacking techniques from all over the world.
CIA cyber specialists used various techniques in order not to leave any data that could be used for attribution of the hacker attack. As a result, it is impossible to identify the true source of an attack, even after thorough criminal examinations. A special
list of dos and don'ts was created for this.
"The CIA's Remote Devices Branch's UMBRAGE group collects and maintains a substantial library of attack techniques 'stolen' from malware produced in other states including the Russian Federation. With UMBRAGE and related projects the CIA cannot only increase its total number of attack types but also misdirect attribution by leaving behind the 'fingerprints' of the groups that the attack techniques were stolen from," WikiLeaks said in a press release.
Among other instruments, the CIA used a utility called Rebound, borrowed from the
Shamoon malware. In 2012, Shamoon was used in hacker attacks on Saudi Aramco's systems and the infrastructure of Qatari gas company RasGas. At the time, Washington said that the malware was of Iranian origin. In turn, Tehran denied the allegations, calling for an international investigation.
The real history of Shamoon is unknown. Perhaps, it was really developed in Iran because its code contained an image of a burning American flag. Moreover, according to experts of Russian multinational cybersecurity provider Kaspersky Lab, the malware was not created by highly qualified programmers.
An updated version of Shamoon was once again used for attacks on Saudi facilities in November 2016 and January 2017.
(A page from the 'Vault 7' archive published by WikiLeaks)
"Russian Hackers"
Another interesting detail revealed from the leaked archive is a vast
list of IP-addresses in different countries, which may have been used by CIA hacking experts. To make a long story short, it may have looked like the cyber attacks were carried out not from the US, but from other countries.
The list also contains several IPs located in Russia. They are assigned to different institutions of the Russian Academy of Sciences, including the Interdepartmental Supercomputer Center and Institute for Space Studies, as well as companies MTS, Sibirtelecom and Sinterra, and even the Russian Interior Ministry.
For example, journalists from Sofia counted 150 Bulgarian IP-addresses. They belong to telecommunications companies, Internet providers, banks and universities.
In late 2016, there were numerous reports about alleged Russian hackers involved in frauds with online ads. Those hackers used IP-addresses belonging to Magnitogorsk Iron and Steel Works, one of the largest steel companies in Russia.
The investigation was carried out by private American company White Ops. The Russian steel company denied the allegations, saying that the addresses have long been obsolete. Moreover, certain IP-addresses reserved by the company were used by unidentified individuals in the US.
Despite the fact that the allegations were rebuffed the incident has been firmly associated with Russia.
For example, if a private or state-run investigation revealed that a US state institution used ID-addresses assigned to the Russian government this would spark a grandiose scandal. Such an attempt has been made, though. In December 2016, the US issued a
report containing a list of suspicious ID-addresses, including those related to "Russian hackers."
Commentators pointed out that at least half of those addresses belong to the Tor anonymous network, which means they could have been used by hundreds of thousands of people around the world.
Priority of Targets
Among the documents dumped by WikiLeaks, there is a
list of questions which must be answered before any hacking operation begins.
Among the questions are types of targeted networks, types of information and files to be obtained, etc. It is also necessary to identify the target of the operation.
"Case Officers are allowed to configure a subset of the full capabilities of the provided tools. To configure a tool for an operation the case officer must answer a set of questions about the operation. The provided tool will then be configured based upon the answers to the questions," the document read.
However, among the possible variants of targets, there are no extremists and criminals. The list contains "foreign intelligence agency," "foreign government entity," as well as "system administrator or comparable technical target."
Perhaps terrorists and potentially dangerous targets can be referred to "other."
Nevertheless, this list clearly indicates the priority targets of CIA cyber operations.